All of us have a basic idea about the fields which interest us the most and would be ideal for career building. The main problem with pursuing our dream profession is finding the right learning programs that can enhance our knowledge and skills in the subject. Those of you reading this article want to establish yourself as an excellent ethical hacker. The journey may not be easy as it seems, but the right ethical hacking course online can help you get through the toughs.
Here is the list of Ethical Hacking courses that are worth your investment and time.
Top 10 Ethical Hacking Online Courses in 2021
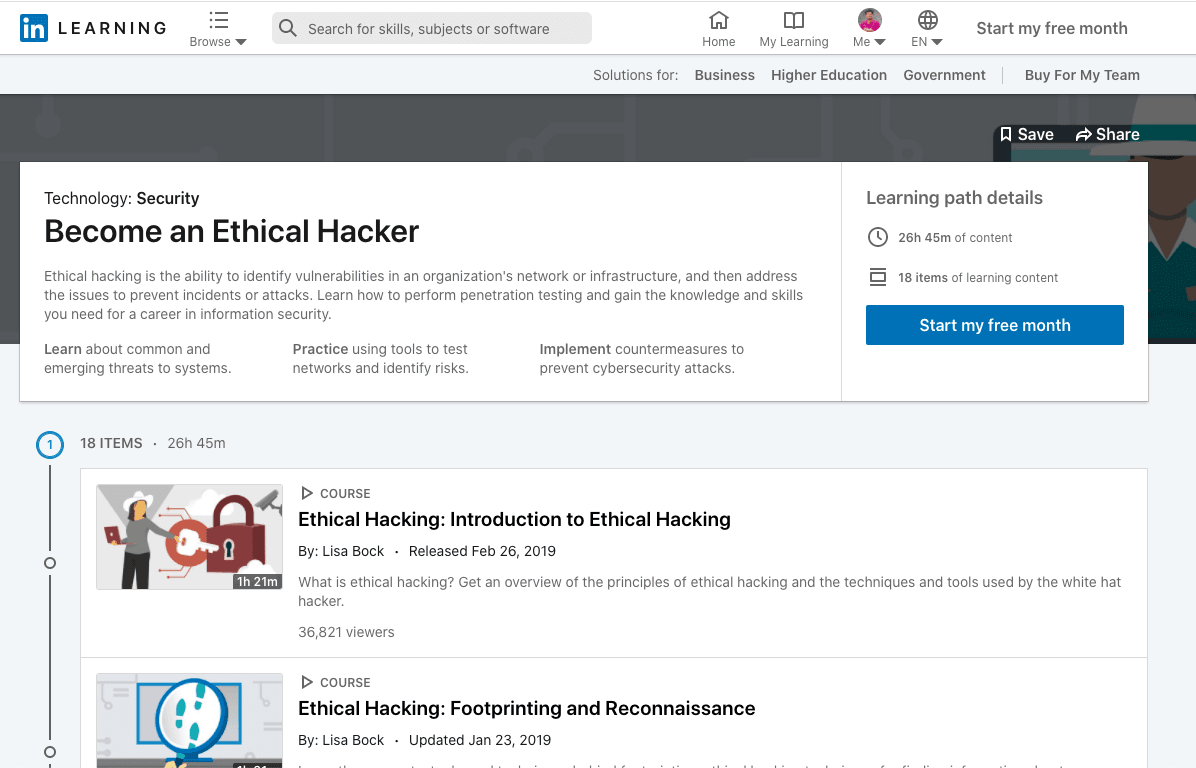
1. LinkedIn Learning- Ethical Hacking Course – Lynda
This learning path Features around 18 learning contents It can be considered as an excellent opportunity for individuals desirous of enhancing their skills and knowledge in the subject. From newbies to experienced professionals, the learning program has something or the other for everyone.
On signing up for this ethical hacking course, you'll have the opportunity to build hacking skills with the help of industry experts like Malcolm Shore, Lisa Block, Scott Simpson, and James Williamson. There are all the major topics included in this learning program, such as:
- Kali Linux
- Enumeration
- Scanning Networks
- Session Hijacking
- Common threats to systems
- Risk identification
- Countermeasuresimplementation
- Reconnaissance and Footprinting, and much more.
If you want to gain the ability to identify vulnerabilities in infrastructure and network of a company, then this specialization will prove out to be an ideal pick. Plus, you'll also learn about the best ways of addressing the issues and eliminate the possibilities of attacks and incidents. The contents are laid out in a simple format so that the students can handle their learning with ease. You may start with the trial version as the first month is cost-free.
Prerequisites: None!
Level: Beginner-Advanced
Rating: 4.8
Duration:26 hours (approximately)
You can signup here.
2. Cybersecurity For Managers: A Playbook
 Introduced by the Massachusetts Institute of Technology, this course is explicitly created for decision-makers and executives. The learning program comes with professionally designed resources that can elevate their skill levels in handling the work environment while ensuring data security.
Introduced by the Massachusetts Institute of Technology, this course is explicitly created for decision-makers and executives. The learning program comes with professionally designed resources that can elevate their skill levels in handling the work environment while ensuring data security.
The specialization comes with a simple playbook so that the executives can create a high-end cybersecurity framework for the security of the business operations. It features the below-listed topics:
- Cybersecurity risk management
- Practical implications of offsets against privacy and security
- Approaches to cybersecurity management
- Decision making for building robust business landscape
- Vocabulary and language for informed talks with CTO and CISO
In addition to the above, the learners also get access to the techniques of defense mechanisms so that they can build an advanced cybersecurity framework according to the industry standards. This e-program is ideal for executives, business leaders, and managers in both non-technical and technical positions aspiring to create an actionable plan for the growth of their organizations.
Prerequisites: Technical knowledge of the subject isn't mandatory.
Level: Intermediate-Advanced
Rating: 4.5
Duration: 6 weeks / 5-6 hours weekly (approximately)
You can signup here.
3. Penetration Testing and Ethical Hacking Course
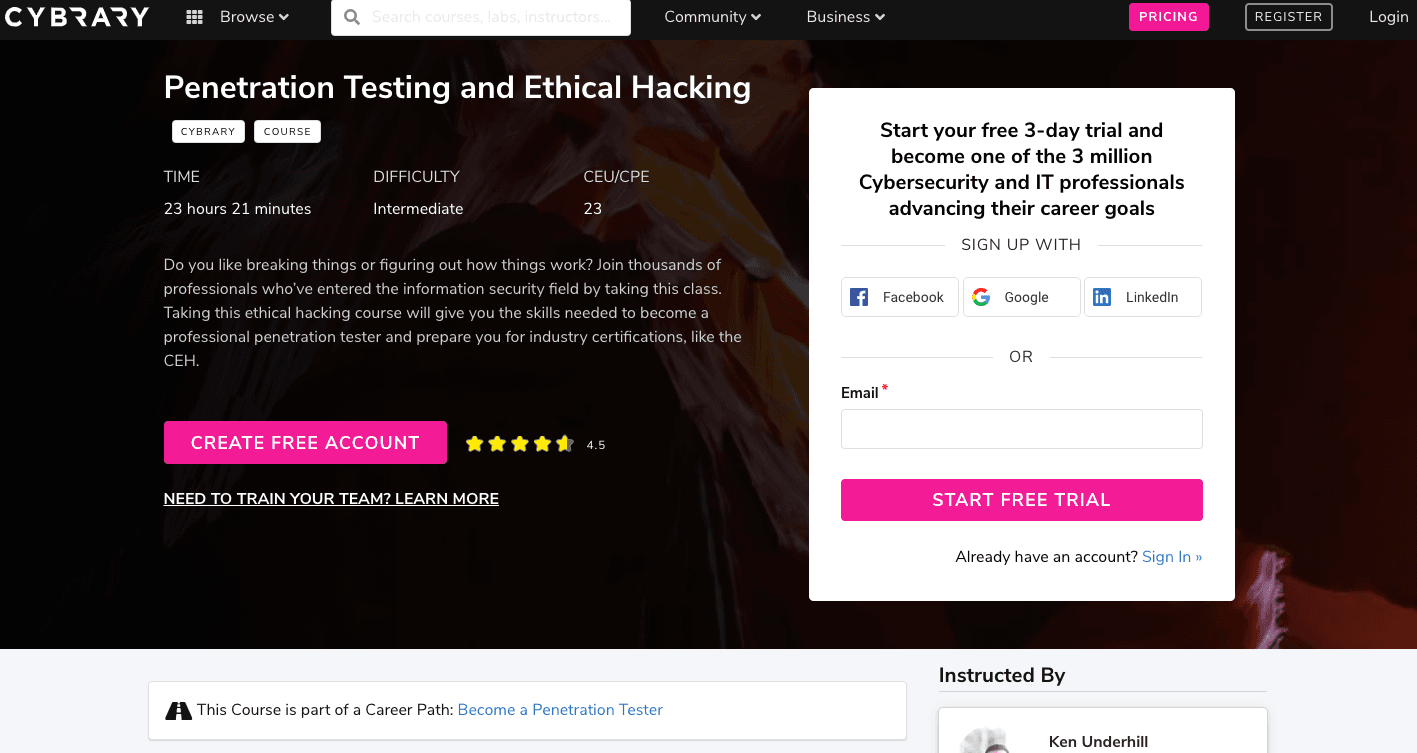 If you are aspiring to become a professional cybersecurity expert, then you should take up this learning program. You'll have the opportunity to learn things from a high-profile Ethical Hacker- Leo Dregier. From introductions to high-level topics, this certification comprises approximately 19 modules.
If you are aspiring to become a professional cybersecurity expert, then you should take up this learning program. You'll have the opportunity to learn things from a high-profile Ethical Hacker- Leo Dregier. From introductions to high-level topics, this certification comprises approximately 19 modules.
This specialization covers the following topics:
- Information Gathering
- Scanning and Enumeration
- Attack and Exploitation
- Vulnerability Identification and Analysis
- Reporting
- PenTest Planning
- Denial of Service
- Sniffing traffic
- Malware Identification and Analysis
- Scanning/Enumeration
- Exploitation
- Reconnaissance
- Session Hijacking
- Post Exploitation Hacking
All the topics are explained in a detailed manner. It also features on-demand video and practical tests so that students can efficiently enhance their knowledge in the certification. And to the top of that, you'll also gain hands-on skills and expertise in this subject as it comes with Virtual Labs.
Prerequisites: The program is designed with the assumption that learners have limited knowledge of the subject.
Level: Beginner-Advanced
Rating: 4.5
Duration: 23 hours (approximately)
You can signup here.
4.Cyber Security Basics: A Hands-on Approach
 Designed by Universidad Carlos III de Madrid's professors, the learning program helps individuals to maintain a strong foothold in the field of cybersecurity. Additionally, you'll also acquire knowledge of prevalent cybersecurity threats and the best ways to deal with them.
Designed by Universidad Carlos III de Madrid's professors, the learning program helps individuals to maintain a strong foothold in the field of cybersecurity. Additionally, you'll also acquire knowledge of prevalent cybersecurity threats and the best ways to deal with them.
Through this specialization, you'll learn:
- Reverse engineering
- Cybersecurity landscape
- Network cybersecurity attacks – management and monitoring
- Malware and advanced persistent threats
- Computer forensics
- Vulnerability pentesting and management
The makers have included around six lectures in this course. The students will get to enrich their portfolio by improving their expertise in essential topics like cyber forensics and monitoring cybersecurity attacks. The best part is that it also covers primary and fundamental issues related to the subject. It is a detailed and well-structured certification.
Prerequisites: No prior technical security knowledge is required.
Level: Intermediate
Rating: 4.5
Duration: 6 weeks / 5-7 hours per week (approximately)
You can signup here.
5. Learn Ethical Hacking From Scratch
 It's a comprehensive Udemy course ideal for the new entrants in the field who have little or no knowledge of penetration testing, hacking, and related topics. Focused on strengthening practical understanding of the subject, the learning program will also give you insights into the interaction between the devices bonded with a network. Additionally, you'll also gain proficiency in setting up a testing lab.
It's a comprehensive Udemy course ideal for the new entrants in the field who have little or no knowledge of penetration testing, hacking, and related topics. Focused on strengthening practical understanding of the subject, the learning program will also give you insights into the interaction between the devices bonded with a network. Additionally, you'll also gain proficiency in setting up a testing lab.
Major topics covered:
- Network penetration testing
- Gaining access
- Post exploitation
- Web application penetration testing
- Kali Linux installation and use
- Linux basics
- Malware analysis
- Discovering and fixing XSS attacks
- Discovering ARP and MITM Spoofing vulnerabilities
- Network Hacking and Penetration Testing.
The learning program features different sections, with each section covering the majors of hacking. Plus, you'll learn about the weaknesses of the target system and practical solutions for exploiting them for hacking. Overall, it is an ideal course for learning the secrets to securing systems.
Prerequisites
- Fundamental knowledge of IT
- No prior skills in hacking or relevant subject needed
- PC or laptop with at least 4GB ram.
- Linux, Windows or OS X
Level: Beginner
Rating: 4.5
Duration: 14.5 Hours (approximately)
You can signup here.
6.Specialization in Hacking For Beginners
 It is a perfect learning program for the individuals who want to learn everything about ethical hacking then consider signing up for this course. Designed by the reputed Hackers, the certification program has gained high popularity among absolute beginners.
It is a perfect learning program for the individuals who want to learn everything about ethical hacking then consider signing up for this course. Designed by the reputed Hackers, the certification program has gained high popularity among absolute beginners.
With this course, you'll acquire expertise in the following topics:
- IP addresses - introduction
- DNS- detailed overview
- Setting up a lab for hacking practice.
- Port scanning
- Understanding hacking vulnerabilities
- Exploiting weaknesses of the target
Available at Udemy, the specialization includes on-demand video, assignments, and other resources so that the learners can learn the concepts without any hassle. Plus, you'll also have the opportunity to try your hand at hacking and enhance your portfolio with practical experience.
Prerequisites:
- Learners should have a fundamental knowledge of computer.
- No prior knowledge of hacking, Linux, or any other programming needed.
Level: Beginner
Rating: 4.5
Duration: 2.5 Hours (approximately)
You can signup here.
7. Cybersecurity Specialization
 If you are a technology person and intrigued by Cybersecurity topics, then this course will prove out to be an ideal choice. It covers all the significant issues related to building a secure system and interactions leveraging cryptography. From software to hardware and human-computer interface, the course focuses on a wide range of topics through the students with every aspect of the field.
If you are a technology person and intrigued by Cybersecurity topics, then this course will prove out to be an ideal choice. It covers all the significant issues related to building a secure system and interactions leveraging cryptography. From software to hardware and human-computer interface, the course focuses on a wide range of topics through the students with every aspect of the field.
Following are the major topics featured in this course:
- Software testing
- Usability
- Cryptography
- Cybersecurity
- Penetration testing
- User interface
- Privacy
- Buffer Overflow
- Fuzz testing
- Number theory
- SQL injection
- Public-key Cryptography
All the concepts are well explained with the help of examples. The course material is designed to help students gain practical experience in handling relevant techniques and tools. Ideally, this learning program is meant for helping the participants develop security-oriented understanding and thinking.
Prerequisites: Basic knowledge of the subject is needed.
Level: Intermediate
Rating: 4.4
Duration: 8 months/2 hours per week (approximately)
You can signup here.
8. The Complete Ethical Hacker Certification Exam Prep Course
 It is an ideal learning program for individuals interested in new technologies. Wit this Udemy ethical hacker course, you will be able to solidify your foundation in hacking as it covers all the topics needed for mastering the subject and clear the Ethical Hacker Certification Exam.
It is an ideal learning program for individuals interested in new technologies. Wit this Udemy ethical hacker course, you will be able to solidify your foundation in hacking as it covers all the topics needed for mastering the subject and clear the Ethical Hacker Certification Exam.
Core topics featured in this certification:
- Technical and business logistics behind penetration testing
- Threats identification
- Internet footprinting
- Cryptography introduction
- Malware protection
- Countermeasures implementation for stopping SQL injections
- Intrusion Detection Systems and Intrusion Prevention System
- Web Application Firewalls
Overall, it has everything needed to gain hands-on experience in ethical hacking while learning the art of defense so that you can keep your system protected from would-be-attackers. The certification is a structured and clear approach of knowing about the ins and outs of overcoming security vulnerabilities, cyber-security, and developing customized protection solutions for various global networks.
Prerequisites:
- Fundamental skills and experience of computers
- Experience in a handling help desk or system administration work
- Familiarity with standards system administrator topics like intrusion detection systems, firewalls, and antiviruses.
Level: Intermediate-Advanced
Rating: 4.3
Duration: 16.5 hours (approximately)
You can signup here.
9. The Complete Ethical Hacking Course: Beginner to Advanced
 The specialization allows the learners to acquire knowledge of penetration testing and ethical hacking while gaining practical experience in the field. Plus, you'll have the opportunity to learn the core topics from Ermin Kreponic - a veteran IT professional. The items featured in this Udemy course include:
The specialization allows the learners to acquire knowledge of penetration testing and ethical hacking while gaining practical experience in the field. Plus, you'll have the opportunity to learn the core topics from Ermin Kreponic - a veteran IT professional. The items featured in this Udemy course include:
- Building virtual hacking environment
- Breaking Linux passwords
- Kali Linux installation
- Linux basics
- Tor, Nmap, VPN, Proxychains, and Macchanger
- Cracking wifi password
- DoS attacks
- SQL injections
- SLL strip and more.
The program is created to help learners enhance their skills and expertise in penetration testing and hacking t activities. It offers detailed insights into securing and protecting the networks from data loss and hackers. There are practical exercises, on-demand videos, and supplement resources in this specialization so that individuals can quickly grasp the concepts.
Prerequisites:
- No prior knowledge of the subject needed.
- A wireless networking interface card
- Good internet connectivity
Level: Beginner-Advanced
Rating: 4.3
Duration: 24.5 hours (approximately)
You can signup here.
10. Hacking and Patching Course
 It is considered as a massive open online course. This Ethical hacking learning program is ideal for learners who want to learn the tricks and techniques of hacking web apps using command injection. Plus, you'll also acquire knowledge of searching valuable info on Linux systems, depositing, and hiding Trojans so that you can use them in the future when needed.
It is considered as a massive open online course. This Ethical hacking learning program is ideal for learners who want to learn the tricks and techniques of hacking web apps using command injection. Plus, you'll also acquire knowledge of searching valuable info on Linux systems, depositing, and hiding Trojans so that you can use them in the future when needed.
The course is designed to help students acquire knowledge of security design patterns, which can help them avoid injection vulnerabilities. From hacking web apps to retrieving user profile passwords and information, there is a lot of exciting learning stuff for students.
The course will make you a pro in the following topics:
- Injection Web App – Attacks and Defenses
- Hack SQL Databases
- Patch Web Apps using Injection SQL Vulnerabilities
- Memory defenses and attacks
- Penetration testing
The program comes with over 20 videos and ten readings, covering all major topics related to the subject. Additionally, you'll also get hands-on training in handling the Nessus scanning tool, Kali Linux Penetration Testing tools, among others. Computer programmers, IT professionals, Security professionals, and Managers can hugely benefit from this specialization.
Prerequisites: Fundamental knowledge of network system security is required.
Level: Intermediate
Rating: 3.9
Duration: 17 Hours (approximately)
You can signup here.
Conclusion
Today, almost every high-profile organization brings on ethical hackers to test and analyze the security of their networks. More and more corporations have begun to invest considerable amounts in strengthening the safety of their software and hardware systems. Certification in ethical hacking is an ideal way to make the most of this increasing demand.